With the online world advancing, the use of the internet is increasing as we find ourselves enveloped in accessible information. We reap the wonderful benefits of this with our abilities to connect with family and friends from around the world, shop online and access endless information. However in doing so we leave behind our own ‘digital identity‘.
Digital Identity: is the information we leave online, the sum of our characteristics. Every time we shop, fill out our email address or even our personal details on Facebook- this builds our online identity. We can have multiple online identities, authentic or fabricated. There are many advantages, but how much control do you have over your identities once online?
The problem:
When posting your information online through social media your information is easy to find if you fail to have adequate privacy settings. Therefore your personal and professional can become blurred, private moments become shared and that information can’t be taken back. In particular, teenagers are shown to actively manage the privacy of their online profiles (Lenhart and Madden, 2007) Everything posted online must be appropriate for all audiences. Although it’s not that simple. Every site we use, accounts we create or searches we make our characteristics get stored to create another identity. It becomes hard to keep track of your information and who has it. Therefore it is not as clear cut as choosing one or multiple identities, we create identities without realizing. This can lead to involuntary sharing; where companies can deduce our identity from a trail we have left. (Internet Society: Video 2, 2017)
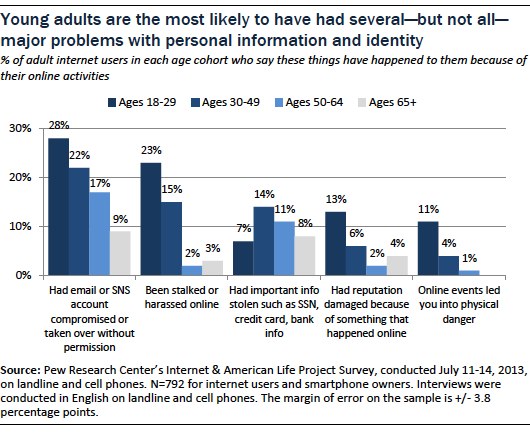
Importance of Identity:
Online identities are useful for firms because they are great marketing tools, and websites use them to help provide a personalized experience, prevent fraud and to provide appropriate adverts (Internet Society: Video 1, 2017). With this in mind, many of the worlds legal frameworks have failed to keep up a regulatory gap, and because of the different cultural views on privacy its impossible to create a global law. (Internet Society: Video 2, 2017) This creates the possibility of third parties accessing your information.
Anonymity argument:
Sites like Facebook are slowly removing the aspect of anonymity, and forcing people to be authentic.
To note: Argument of community 2:31, Dusty Argument 5:24 and from 7:25 see his response to the attacks on anonymity.
However, online users are less likely to interact with profiles they do not know or trust (Costa and Torres, 2011).
Therefore, managing our identities is vital in order to keep your privacy and security.

Word count: 398
Bullingham, L. and Vasconcelos, A. (2013). ‘The presentation of self in the online world’: Goffman and the study of online identities. Journal of Information Science, [online] 39(1), pp.101-112. Available at: http://journals.sagepub.com/doi/abs/10.1177/0165551512470051 [Accessed 21 Feb. 2017].
Costa, C. and Torres, R. (2011). To be or not to be, the importance of Digital Identity in the networked society. Revista Educacao, Formacao & Technologias. [online] Available at: http://eft.educom.pt/index.php/eft/article/view/216/126 [Accessed 21 Feb. 2017].
Internet Society, Video 1: Online Identity – An Overview, 2017 Available at: http://www.internetsociety.org/online-identity-overview#overlay-context=
Internet Society, Video 2:Protecting Your Privacy, 2017 Available at: http://www.internetsociety.org/protecting-your-privacy
Krotoski, A. (2012). Online identity: is authenticity or anonymity more important?. The Guardian. [online] Available at: https://www.theguardian.com/technology/2012/apr/19/online-identity-authenticity-anonymity [Accessed 22 Feb. 2017].
Lenhart, A. and Madden, M., 2007. Teens, privacy and online social networks: How teens manage their online identities and personal information in the age of MySpace.
Rainie. L, Kiesler.S, Kang. R, Part 5: Online Identity Theft, Security issues, and Reputational Damage, 2013, http://www.pewinternet.org/2013/09/05/part-5-online-identity-theft-security-issues-and-reputational-damage/
Ted Talks, The case for anonymity online | Christopher “moot” Poole, 2010 Available on: https://www.youtube.com/watch?v=a_1UEAGCo30&t=607s.



Hi Emily, I think this is a brilliant blog post with great clarity shown throughout. I am particularly drawn to your point about third parties accessing your information. A concern constantly in the headlines! Upon further reading around the topic I came across the work of Jajodia et al. (2011) who states “intrusions by dedicated actor groups appear to have become more persistent, threatening and global”. Do you feel that this is due to the inability to create global law that you have mentioned, or do you think it could be an issue with computing (hardware and software) itself?
I look forward to hearing your thoughts on this.
Harriet
LikeLike
Hi Harriet, thank you for your lovely comments. To address your question, I am leaning towards the problem of global law. As of the many cultural differences the world is quite resiliant towards a ‘global law’. Although computing itself may be an issue too, the field is constantly growing and changing and improving! I think that the minority who are able to infiltrate security setting and so on are just that- a minority! As it is still an issue, I feel that the lack of ability to produce strict laws and punishments for third parties and accessing your private information is the main pitfall in this problem highlighted by Jajodia et al.
Thanks again for your comment,
Emily
LikeLike
Hi Emily,
No problem. Thank you for getting back to me. It’s really interesting to hear your view! I agree with you totally but would also argue it could be down to a mixture of both. In my eyes they almost go hand in hand thus have equal downfalls.
Harriet.
LikeLike
Very valid, pithy, suiccnct, and on point. WD.
LikeLike
I would have to agree with your point, they both are very closely linked!
LikeLike
RB, Did he ask you to pull his finger? Unlike ancient Greek, I can read French. I would like the new translation, or to obtain the French text it was compiled from. Great brain exercise to read other languages. Why it is corasovenritl to look at more than one account of the crucifixion, I will leave for others to say. There were an awful lot of crucifixions in Judea, and it was not unusual for everyone in the crowd to be reluctant (to say the least) to speak up for anyone who was executed for political reasons. Those Romans were savages, the damn Christ Killers! : P
LikeLike